Excellent software and practical tutorials
WordPress is anti-refreshing, the CPU of a small website is inexplicably full, and the website reports a 502 error. What happened?
WordPressAnti-refresh, WP security is the first priority. The most distressing thing for many friends who build websites is that when the website has no traffic, they rack their brains to do traffic diversion and publicity. After the website has traffic, good and bad things come together. The website was attacked inexplicably. Now many websites are small blogs built with wordpress. Usually there are only a dozen people online at the same time. Why is the server CPU running at full 100%, and the memory also soars to the top in an instant. Many websites use foreign hosts that are billed by traffic. After a few days, the traffic runs out and the website cannot be opened.
You may have encounteredSearch Attack.
What is a malicious search attack?
ThisMalicious searchesThe attack is actually very simple. It is to continuously launch bad keyword search visits to the website through the established URL structure. For example, the search URL structure of WordPress is Domain name/?s=search term, and may also push the visited addresses to major search engines to speed up the inclusion of these malicious URLs. In this way, your website will become a channel for these lawless people to spread bad information, which is very unfavorable to the website ranking, and may even be directly K-stationed by search engines.
Recently, many WordPress websites have encountered similar problems. After exploring the reasons why the website was attacked, we found the following reasons.
- Attacks for profit:yourSEOIf you optimize well, you will be ranked in front of some websites. If your keywords are eliminated and you lose the engine ranking, naturally no one will attack you. It is usually used for DDOS attacks. Currently, DDOS attacks on the Internet are expensive. The traffic on search engines is very small. Most of the traffic on the Internet is on mobile devices, so PC websites have rarely encountered such attacks in recent years.
- Attacks initiated by website diversion:This type of attack is often encountered on websites built with WordPress. It maliciously increases the keyword search volume. Because your search ranking is relatively high, the search engine will naturally include new links of your website in seconds. WordPress search can submit any content in the URL, and then the search engine will quickly crawl every submitted link, causing huge pressure on the server CPU.
- Malicious search attacks:This malicious search attack is actually very simple. It is to continuously launch bad keyword search visits to the website through the established URL structure. For example, the search URL structure of WordPress is domain name/?s=search word, and it may also push the visited address to major search engines to speed up the inclusion of these malicious URLs. In this way, your website will become a channel for these criminals to spread bad information, which is very unfavorable to the website ranking, and may even be directly K-stationed by search engines.
- SQL Injectionattack:This type of attack is similar to a malicious search attack. It continuously submits various vulnerability codes for detecting SQL registration in the search. This type of attack is very common in WordPress, and many websites have been attacked. The current WordPress is relatively safe, and the new version does not have SQL injection vulnerabilities. This type of attack continuously submits code, and the page after the code is submitted will be caught by the search engine.GoogleA smarter search engine will filter out such pages, but Bing will consider it as a suspected malicious website refresh, which will cause abnormal indexing of new website content within a short period of time. This problem can be solved by sending an email directly to the Bing administrator.
If the webmaster does not check the status of the website regularly, it is likely to suffer. If the website is blocked by the search engine, you can write to the administrator of the search engine.
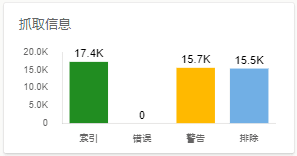
The main reason for wordpress search spamming and malicious search attacks is to promote some shady websites. These websites will use any means to promote themselves.
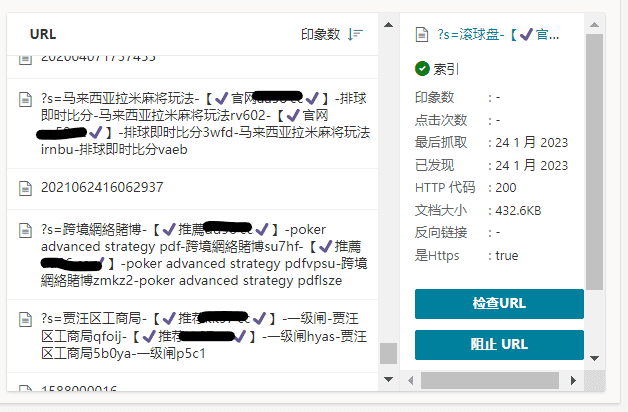
Let's talk about WordPress when you encounterBrush SearchLet’s find out the solution when the problem occurs, and at the same time analyze and understand the principle of wp search brushing.
The search function of wordpress is very simple. Just add "?s=" after the domain name, and then fill in the keywords you want to search for. For example:
https://uzbox.com/?s=office
Copy the URL into the address bar of the browser to query the website forofficeRelated content. The normal search on the website is to enter keywords in the search box and then submit the search through the form.
Since WordPress can search by entering a URL in the address bar, an attacker can write a simple script to refresh the search continuously. Since the search will index information from the database, the database on the server will eventually run out of CPU.
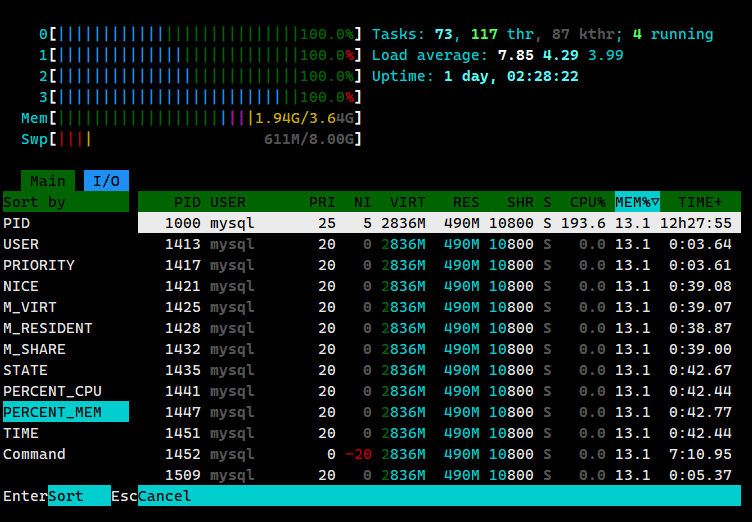 Most of these search attacks are aimed at increasing the search keyword rankings and directing traffic to black and gray industry websites. In many cases, the server crashes, which is something the attackers don’t want to see. The attackers also didn’t expect that some servers are so vulnerable to being refreshed. If the refresh frequency is high, the server will crash!
Most of these search attacks are aimed at increasing the search keyword rankings and directing traffic to black and gray industry websites. In many cases, the server crashes, which is something the attackers don’t want to see. The attackers also didn’t expect that some servers are so vulnerable to being refreshed. If the refresh frequency is high, the server will crash!
The so-called "malicious search attack" is a black hat SEO method that uses WordPress site search to optimize the number of external links for certain long-tail keywords in order to increase search weight (as shown in the picture above). If the website administrator does not check the website regularly, he or she is likely to suffer.
Now that we know the attacker's attack method and the idea of sweeping searches, let's solve this problem.
A black hat SEO method that uses the built-in search function of WordPress to optimize certain long-tail keywords for promotion purposes..
Block malicious searches
To block malicious searches, we first need to monitor what malicious search terms the other party uses, so we first install WP Search Analytics Plug-in, on the search analysis page below the dashboard, we can see the search terms.
Add the following code tofunctionsIn the .php file, it is recommended to use a plug-in to add it!
add_action('admin_init', 'search_ban_key'); function search_ban_key() { add_settings_field('search_key', 'Search keyword blocking', 'search_key_callback_function', 'reading'); register_setting('reading','search_key'); } function search_key_callback_function() { echo 's'],$Key) != false ){ wp_die('The keywords you entered have been blocked! Please do not conduct search attacks anymore! Thank you!'); } } } } }Then add the keywords you want to block in the reading page of the background settings menu.
Commonly blocked keywords can be found at:https://github.com/jkiss/sensitive-words
Revise Robots.txt rules, add a ban on engine indexing site search links.
Disallow: /?s=* Disallow: /*/?s=*\ Disallow: /search/
Limiting the search frequency can be set in the firewall, the number of page visits per second.
Solution to wordpress anti-refresh
Most of these web-refresh attacks areCC attack. Unlike DDOS attacks, DDOS attacks use a large number of zombie IPs to centrally deny service access to a website, and finally the huge access traffic causes the server network to be blocked and paralyzed. If you encounter a DDOS attack, you need to use CDN distributed nodes to solve it, which of course is also very expensive.
CC attacks are generally easy to resolve. Just find out the attacker's attack method and then contain it.
We already know that refresh access is done through search, so let’s talk about how to solve it.
Limit the number of times the same IP address can access the website
Need toNginxConfigure the HttpLimit module in HttpLimit to control the number of concurrent connections for a session based on conditions. (For example: limit the number of concurrent connections for each IP.)
http{ #limit_zone one $binary_remote_addr 10m; limit_req_zone $binary_remote_addr zone=req_one:10m rate=10r/s; server{ #limit_conn one 1; limit_req zone=req_one burst=1; } }There are two ways to use the module configuration above, which can be set according to different situations.
Method 1:
limit_zone one $binary_remote_addr 10m;
Here one is the name of a limit_zone, $binary_remote_addr is the variable that replaces $remore_addr, and 10m is the space for session state storage.
limit_conn one 1, limit the number of concurrent client connections to 1
Method 2:
limit_req_zone $binary_remote_addr zone=req_one:10m rate=10r/s;
rate=10r/m means that each address can only request 10 times per minute, that is, according to the token bucket principle, burst=1 has a total of 1 token, and only 10 tokens are added per minute.
After 1 token is issued, any additional requests will return 503.
With nodelay, requests exceeding the burst size will directly return 503
If this field is missing, a large number of TCP connection requests will be waiting.
limit_zone two working conditions
limit_req zone=one burst=10;
By default, this is configured so that each request will have a delay of 0
limit_req_zone $binary_remote_addr zone=one:100m rate=10r/m;
That is, there are 10 tokens available for users every minute, and the time for each request is 60/10, so the time for each request is 6s.
limit_req zone=one burst=10 nodelay;
Add nodelay configuration, so that the access is based on your network conditions. After 10 accesses in one minute, the server directly returns 503.
imit_req_zone $binary_remote_addr zone=one:100m rate=10r/m;
That is, there are 10 tokens available for users every minute, and the URL will be accessed according to the network conditions. If more than 10 tokens are used in one minute, the server returns 503 and waits for the next minute to receive the access token.
After configuring the HttpLimit module, restart nginx.
Install WordPress Security Plugin
In WordPress, security plugins are essential. Without security plugins, you are naked on the Internet. Recommended installation Wordfence Security plugins that provide real-time visibility into the IP addresses logged into your site, including an endpoint firewall and malware scanner, built from the ground up to protect WordPress. The most popular WordPress firewall and security scanner

It is highly recommended that WordPress users install the Wordfence firewall.
GPLThe functions of the premium version can already meet the normal needs of an ordinary website.

The website encountered an SQL search injection attack. The attacker continuously used the remote server to launch injection code tests on the website and continuously entered the injection code in the search. If there is no Wordfence firewall, it will greatly increase the server CPU load. InstallWordfenceBehind the firewall, you can check and view the problematic IP at any time, and the firewall can also intelligently block malicious IP addresses. Even thousands of code injection scans will be blocked by the firewall. It will not affect the CPU, nor increase the computing cost of the server.
We have always believed that the Internet is very safe, but there are thousands of malicious attacks every day. Even if we think some hacker attacks are meaningless, such attacks do exist, so it is imperative to install a web firewall. Recommended installation:
Wordfence Security – Firewall, malware scanning and login security
WordPress security requires a dedicated team of analysts to research the latest malware variants and WordPress vulnerabilities, translate them into firewall rules and malware signatures, and publish them to customers in real time. Wordfence is widely regarded as the #1 WordPress security research team in the world. Our plugin offers a comprehensive set of security features, and our team’s research powers our plugin and provides the level of security we are known for.
At Wordfence, WordPress security isn’t a division of our business – WordPress security is everything we do. We employ a global 24/7 dedicated incident response team, providing our priority customers with a 1-hour response time to any security incident. Our global security team never sleeps, and we run a sophisticated threat intelligence platform to aggregate, analyze the latest security threats, and conduct groundbreaking security research.
Wordfence Security Includes an endpoint firewall, malware scanner, powerful login security features, real-time traffic view, and more. Our Threat Defense Feed provides Wordfence with the latest firewall rules, malware signatures, and malicious IP addresses to keep your website safe. Rounded out by 2FA and a suite of additional features, Wordfence is the most comprehensive WordPress security solution available.
WORDPRESS FIREWALL
Web Application Firewall identifies and blocks malicious traffic. Built and maintained by a large 100% team focused on WordPress security.
[Premium] Real-time updates of firewall rules and malware signatures via threat defense feed (30-day delay in Free Edition).
[Premium] Real-time IP Blocklist blocks all requests from the most malicious IPs, protecting your website while reducing load.
Protect your site at the endpoint with deep integration into WordPress. Unlike cloud alternatives, it doesn’t break encryption, can’t be bypassed, and won’t leak data.
An integrated malware scanner blocks requests that contain malicious code or content.
Prevent brute force attacks by limiting login attempts.
WORDPRESS SECURITY SCANNER
The malware scanner checks core files, themes, and plugins for malware, bad URLs, backdoors, SEO spam, malicious redirects, and code injections.
[Premium] Real-time malware signature updates via the Threat Defense Feed (30-day delay in Free Edition).
Compares your core files, themes, and plugins with those in the WordPress.org repository, checking their integrity and reporting any changes to you.
Repair changed files by overwriting them with their original, pristine versions. Delete any files that are not part of the Wordfence interface.
Checks your site for known security vulnerabilities and alerts you if any issues arise. It also alerts you to potential security issues when plugins are shut down or abandoned.
Check your content safety by scanning file contents, posts and comments for dangerous URLs and suspicious content.
[Premium] Check if your site or IP has been blacklisted for malicious activity, spam generation, or other security issues.
Login Security
Two-factor authentication (2FA), the most secure form of authentication to remote systems, is available through any TOTP-based authenticator app or service.
Login page CAPTCHA prevents robots from logging in.
Disable 2FA or add 2FA to XML-RPC.
Block administrator logins using known compromised passwords.
WORDFENCE CENTER
Wordfence Central is a powerful and effective way to manage security for multiple sites in one place.
Efficiently assess the security status of all your websites in a single view. View detailed security findings without leaving Wordfence Central.
Powerful templates make configuring Wordfence a breeze.
Highly configurable alerts can be sent via email, SMS or Slack Send. Improve the signal-to-noise ratio by utilizing the severity level options and the daily summary options.
Track and alert on critical security events, including administrator logins, compromised password usage, and spikes in attack activity.
Free for unlimited sites.
Security Tools
With Live Traffic, monitor visits and hacking attempts in real time that don't show up in other analytics packages; including the source, their IP address, time of day, and time spent on your site.
Block attackers by IP or build advanced rules based on IP ranges, hostnames, user agents, and referrers.
Wordfence Premium Provides country blocking functionality.
Free download WordFence Premium 7.8.2 activated Chinese version
Modify the default search URL in WordPress
Modify the default search link. The default search of WordPress is "?s=". The default link is easily scanned. You can rename the search link. Although it has little significance in terms of security, it may increase the inclusion of search engines.
For specific modification methods, please refer to:Modify the default search URL in WordPress to increase the number of SEO inclusions!
Install HttpGuard on nginx to prevent CC attacks
HttpGuard is a tool based on nignx lua. Its function is relatively simple, but very powerful and effective. Its main function is still to defend against CC attacks. It mainly uses technical means to detect whether the visitor is a valid browser and whether it supports jumps to determine whether it needs to be intercepted. But HttpGuard has another special ability, which is to monitor the real-time number of connections to determine whether the anti-attack module needs to be enabled.
Before installing HttpGuard, you need to install OpenResty.
exist CentOS Add the openresty repository to the system so that it will be easier to install or update our packages in the future.See more system installation methods
wget https://openresty.org/package/centos/openresty.repo sudo mv openresty.repo /etc/yum.repos.d/ sudo dnf check-update
Then you can install the software package, such as openresty, as follows:
sudo dnf install -y openresty
If you want to install the command line tool resty, you can install the openresty-resty package like this:
sudo dnf install -y openresty-resty
Install compilation tools and related dependencies.
dnf install pcre-devel openssl-devel gcc curl
OpenResty has been installed successfully. You have installed OpenResty to the /usr/local/openresty directory (this is the default setting)
After downloading, unzip the file and upload it to the server root directory.
cp -r HttpGuard/ /etc/nginx
Copy the folder to the Nginx installation directory. The nginx directory installed by dnf is in /etc/nginx, and the compiled and installed nginx directory is generally in /usr/local/nginx. Before copying, confirm the nginx installation directory.
After copying, edit the nginx configuration file nginx.conf .
#Add the following in the http block lua_package_path "/etc/nginx/HttpGuard/?.lua"; lua_shared_dict guard_dict 100m; lua_shared_dict dict_captcha 70m; init_by_lua_file '/etc/nginx/HttpGuard/init.lua'; access_by_lua_file '/etc/nginx/HttpGuard/runtime.lua'; lua_max_running_timers 1;
The above are some solutions for WordPress websites being attacked by malicious searches. Malicious searches are a problem that most WordPress website owners will encounter. After all, malicious searches will increase the pressure on our servers and even affect the weight of the website in search engines, so you still need to pay attention.





Recommend using Wordfence Security